I have recently been working on PreEx, a pre-exploitation intelligence gathering program.
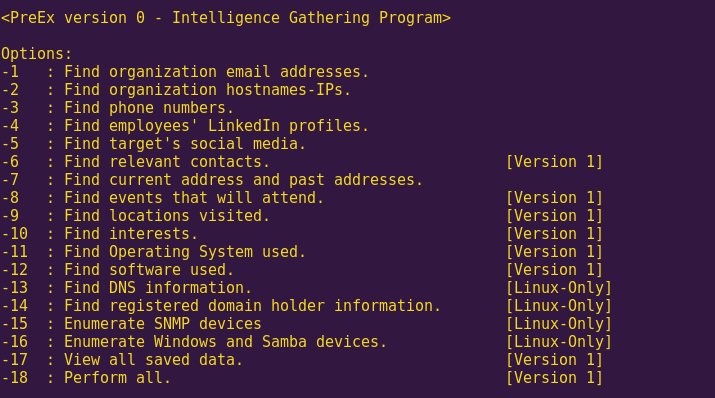
My goal with PreEx is to make it easier to gather all the information necessary in order to launch a targeted attack. In combination with other tools such as Tuoni and Cryptan, PreEx can be used to better fingerprint targets and carry out attacks more efficiently.
The use of this tool is to be limited to testing purposes under legal authority.
The current version of PreEx is version 0.
Current capabilities:
* Organization email addresses
* Organization hostnames-IPs
* Target Phone numbers
* Employee social media profiles
* Target Social media profiles
* Current and past addresses
* DNS information
* Registered domain holder information
* SNMP device enumeration
* Samba device enumeration
Future capabilities:
* Relevant contacts
* Events to attend
* Locations visited
* Interests
* Operating System used
* Software used
More functionalities and capabilities will be added in the future.